10 february 2026 14h00-14h30
Davide De Carvalho & Filippo Tosato (MECA)
Military jets and firearms generate some of the most intense sounds encountered in operational environments, producing acoustic signatures that pose significant risks to both personnel and surrounding communities. Understan...
10 february 2026 13h30-14h00
Ken Hasselmann (MECA)
This presentation provides an overview of current challenges and ongoing research in military robotics across ground, air, and maritime domains. It focuses on the use of autonomous and semi-autonomous robotic systems to support operations such...
10 february 2026 13h00-13h30
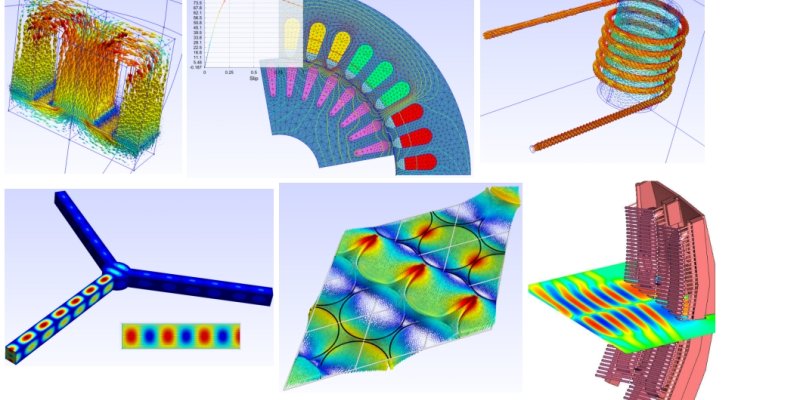
Philippe Lamalle (PHYS)
The finite element method (FEM) is probably best known for its numerous applications in structural mechanics and mechanical engineering. Over the past four decades, it has also gradually become ubiquitous for the modelling of engineering probl...
2 December 2025 14h00-14h30
Bogdan Stirbu (ABAL)
Barrel erosion is a critical factor influencing firearm performance, reliability, and service life. This study investigates erosion phenomena in 5.56×45 mm caliber barrels under both laboratory-controlled and operational wear replication condition...
2 December 2025 13h30-14h00
Bachir Belkassem (STEE)
Unexploded ordnance (UXO), particularly legacy air-dropped bombs, remains a significant hazard in post-conflict zones, especially in urban environments. Decades after World War II, thousands of unexploded bombs are still discovered annually, of...
2 December 2025 13h00-13h30
Bart Simoens (CHCH)
Although access to explosives is supposed to be very limited, people with bad intentions are resourceful. In order to protect people and infrastructure from attacks with explosives, detection of these explosives before they are put to use is crucia...
4 November 2025 14h00-14h30
Dr. Ann-Katrien Oimann (SCGW)
Artificial intelligence (AI) is increasingly used across a wide range of domains, including the military. As we move toward more advanced, second-generation AI systems, their growing autonomy in decision-making processes raises pressing e...
4 November 2025 13h30-14h00
Vincent Joassin (COST)
Can threat perceptions embedded in political narratives serve as a determinant for assessing military expenditure? While existing research often relies on objective indicators—such as geographic proximity or the military spending of adversaries—...
4 November 2025 13h00-13h30
Sten Delvaux (DEML)
In today’s rapidly changing world, military leaders must navigate uncertainty, complexity, and constant change. Although leadership scholars and practitioners widely acknowledge the importance of adaptive leadership, it remains poorly defined and u...
9 September 2025 14h00-14h30
Alexander Borghgraef (CISS)
The use of Radio-Frequency (RF) technology has been ubiquitous on the battlefield ever since its introduction in WW1. From the early wireless telegraphy and morse code, it has evolved to be used in the transmission of voice, data, images a...
9 September 2025 13h30-14h00
Dr. Ir. Pouyan Ebrahimbabaie Varnosfaderani (CISS)
The space domain is rapidly militarizing as major space powers enhance their counterspace capabilities. The Russia-Ukraine war underscored the vulnerabilities of commercial Satellite Communications (SATCOM) solution...
9 September 2025 13h00-13h30
Charles Beumier. dr. (CISS)
As part of a project subsidized by the SPF Economy and involving the Belgian Ministry of Defence, Orange Belgium, and Streamwide, 5G was evaluated as a telecommunications solution for the MoD. Specifically, the CYLAB team at the RMA was ta...
3 June 2025 14h00-14h30
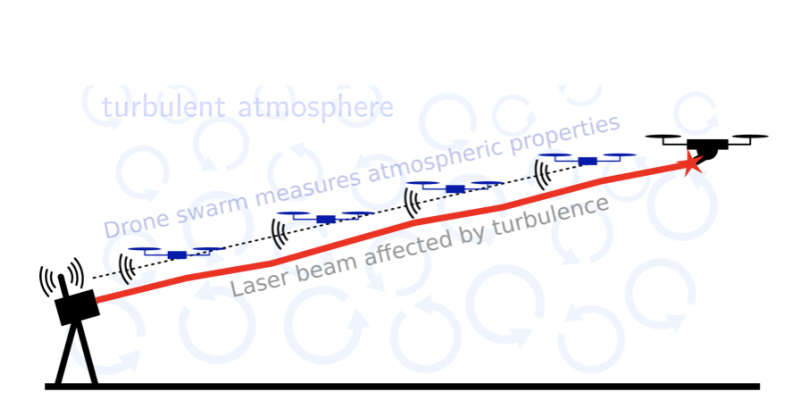
Karel Desnijder (CISS)
Atmospheric characterization is crucial for optimizing laser propagation and enhancing the performance of optical systems in open-air environments. Traditional measurement methods often struggle to capture distributed atmospheric parameters, especia...
3 June 2025 13h30-14h00
Julien Decharneux (SCGW)
This webinar will explore the evolving landscape of spiritual-existential care in the Belgian Armed Forces, focusing on both the reform of military chaplaincies and the development of tools to assess Spiritual Fitness, all within a broader NATO a...
3 June 2025 13h00-13h30
Zacharie Paquet (DLD-bio)
Ricin is a lethal and readily available plant toxin from Ricinus Communis. Recent events, such as the Cologne terrorist plot, have continuously demonstrated the need for qualitative and readily available tools to detect this potential biowarfare...
11 February 2025 14h00-14h30
Daniela Doroftei (MECA) ir.
The increasing availability and accessibility of Unmanned Aerial Systems (UAS) pose significant challenges for defence actors and law enforcement agencies tasked with managing the security of lower airspace. The need for robust and reliabl...
11 February 2025 13h30-14h00
dr. Letitia Fernandez Velasco (CHCH)
CBRN (Chemical, Biological, Radiological, and Nuclear) threats stem from natural disasters, accidents, or intentional incidents like terrorism, with deliberate threats persisting or rising in recent years. The COVID-19 pandemic hi...
14 January 2025 14h00-14h30
Skralan Hosteaux, M.Sc (Chair of Mathematics)
Hyperspectral imaging (HSI) allows capturing detailed spectral information for each pixel within the FOV of your camera. Unlike traditional imaging systems that capture data in three primary bands (red, green, and blue), H...
14 January 2025 13h30-14h00
Johan Massart, M.Sc (Chair of History)
Since 1945, Belgium has participated in a long series of military operations abroad, including peacekeeping and peace-enforcing missions under the auspices of the UN or NATO, but also bilateral or unilateral interventions in for...
3 December 2024 14h00-14h30
Mariko Matsuzaki, M.Sc (Department of Life Sciences)
Training is essential for building and sustaining military capabilities, with trainers and training centers serving as the foundation of this endeavor. However, high retirement rates among experienced trainers pose...
3 December 2024 13h30-14h00
Lise Blokerije & Delphine Resteigne (Chair of Sociology)
Recruiting new military personnel has been a top priority for Belgian Defence, especially with around one in five of its current workforce set to retire in the coming years. However, the significant costs and ti...
5 November 2024 13h30-14h30
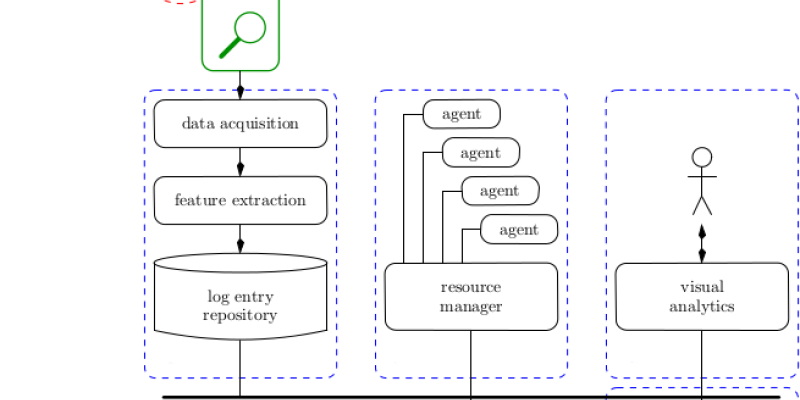
Yoann Arhant (CISS)
Deep learning models can be powerful tools, but they are often bound to fail unexpectedly with degenerate data, and it becomes all the more critical in military applications. Therefore, this is crucial to check and understand model outputs with in...
8 October 2024 13h30-14h30
Gregory Kegels & Grith Skovgaard Ølykke (DEML)
The current geopolitical situation highlights the importance of strategic autonomy, especially in a domain such as defence and security. To support an effective implementation of the Belgian Defence, Industry and Research...
10 September 2024 13h30-14h30
Georgios Kechagiadakis
In the wake of increasing global security challenges, the need for advanced research into the dynamics of blast effects and protective structures has never been more critical. Over the past decades, the escalation in asymmetric warfare and ter...
11 June 2024 14h00-14h30
Georgi Nikolov
With the rapid growth of the Internet, network infrastructures need to keep pace and develop their cyber security awareness through the use of different Intrusion Detection (IDS) and Prevention Systems (IPS). These systems often are dependent on signature-...
11 June 2024 13h30-14h00
Arnaud Stoz
When developing software, developers and companies usually rely on numerous external libraries. According to GitHub State of the Octoverse Report 2019, open-source projects have an average of 180 package dependencies. The same goes for commercial and closed-s...
14 May 2024 14h00-14h30
Dr. Andrew Rebera
A great deal of military technology aims at enhancing risk-asymmetry, i.e. at reducing risks faced by the militaries that deploy it and/or increasing the risks imposed upon their enemies. For example, unpiloted aerial vehicles (UAVs) and (semi-)autonom...
14 May 2024 13h30-14h00
Vita Glorieux, M.Sc., Salvatore Lo Bue, Lieutenant-Colonel, Ph.D & Dr. Martin Euwema
Military personnel undergo rigorous training to navigate the complexities of deployment cycles. While research and practice have given significant attention to interventions during initia...
9 April 2024 13h30-14h30
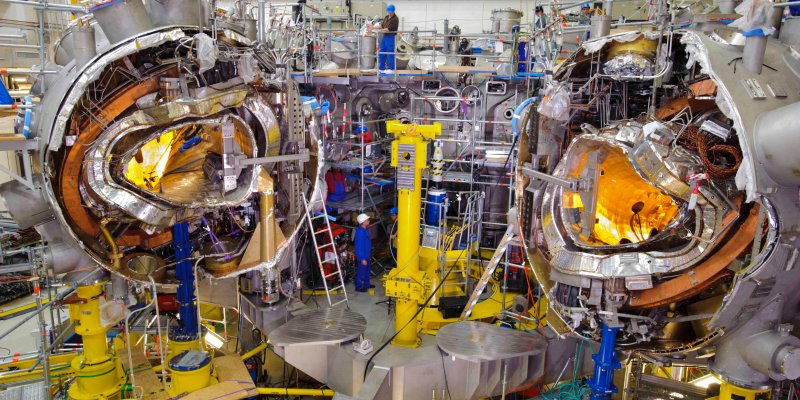
by Dr K. Crombé & A. Goriaev
The idea of nuclear fusion employment as an energy source attracts more and more attention, reflecting the current socioeconomic situation. It stimulates the further development of different classical experimental fusion devices and the fast...
12 March 2024 13h30-14h30
by Dr Ir Angel Miranda-Vicario
Body armour systems, like bullet-resistant vests or fragment-resistant helmets, are tested extensively according to different norms and standards before being introduced for service, in order to ensure these systems can provide the require...
13 February 2024 13h30-14h30
by Mr. Djamal Belmehdi
Dual-use substances or those used to synthesize known homemade explosives (HME) are strictly controlled. Nevertheless, tertiary explosives are generally not considered as explosives by international regulations. As they are exceptionally diffic...
09 January 2024 13h30-14h30
Mattia Stasolla, PhD
Geospatial intelligence has become an important component of modern warfare. Thanks to satellite images, it is nowadays possible to monitor large areas of interest with a short revisit time, collecting valuable information that would be otherwise...
05 December 2023 13h30-14h30
by Bart De Clerck (MWMW)
Open source intelligence (OSINT) is a valuable tool for military information gathering and decision-making. It can be used to uncover actionable insights, verify secret information, and provide near-real-time information. As seen in the recen...
07 November 2023 13h30-14h30
by Sara Van Hoeymissen, Nick Houttekier & Eleftheris Vigne (DEML)
In a world of rising geopolitical tensions, economic relations between states are becoming an arena of conflict. Recent crises, such as the COVID-19 pandemic and the Russian invasion of Ukraine, have d...
03 October 2023 13h15-14h15
by Prof Delphine Resteigne & Wendy Gomes (Chair of Sociology)
Having been considered as “uniformed” organizations for a long time, military organizations are increasingly focusing on the integration and inclusion of minority groups. They do this in order to attract an...
12 September 2023 13h30-14h30
by Maj. Nathalie MARCUS
La menace terroriste en Belgique et en Europe n’est pas un phénomène nouveau. Cependant, cette menace est devenue nettement plus palpable depuis les attentats de 2001 aux Etats-Unis suivis de plusieurs attentats sur le sol européen ces vingt...
06 June 2023 13h45-14h15
by Cdt Dr Ir Romuald VAN RIET
Ammunition ageing has always been an issue, especially when ammunition is stored in hot climates. Ammunition ageing can lead to deterioration of the weapon's ballistic properties, damage to weapon systems and, in extreme cases, spontaneous...
06 June 2023 13h15-13h45
by Cdt Dr Ir Romuald VAN RIET
Tertiary explosives are a serious and emerging threat in the context of homeland security, counterterrorism and counter-improvised explosive devices, and are therefore the subject of this research conducted in collaboration between the RMA'...
02 May 2023 13h00-14h00
by Dr. J. Van Cutsem & Prof. M. Van Puyvelde
“It is not the strongest, but the most adaptable that survive”, wrote Charles Darwin in 1859. A lot of our military operators need to function in what is called a vulnerable, volatile, uncertain, complex, and ambiguous (VUCA)...
04 April 2023 13h00-14h00
by B.G. Marinus & B. Janssens
Flows and the associated mass and energy transfer as well as forces have been studied from the dawn of engineering for their prevalence around us. The movement of gases and fluids govern an extremely wide set of applications ranging from l...
07 March 2023 13h00-14h00
by dr. Jef ONGENA & Lt. Kol. Maarten VERGOTE
The consequences of the massive expansion of solar and wind energy for electricity generation are illustrated based on results from the German Energiewende of the past 5 years. The large variability in production leads to pe...
07 February 2023 13h30-14h30
by dr. Cyril ROBBE
Through the years, Non-Lethal Weapons (NLW) are becoming more and more widespread. The concept is indeed appealing: neutralizing the threat with a reduced level of deployed force, mitigating unnecessary injuries or casualties and reducing the pote...
10 January 2023 13h30-14h00
by dr. Helena Bruyninckx
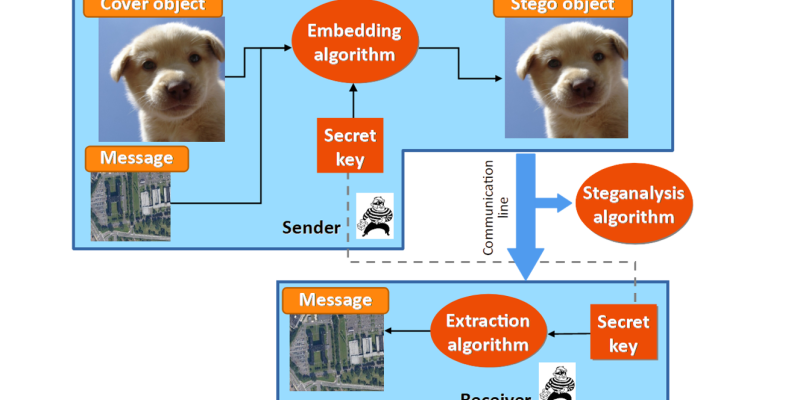
Due to the widespread availability of Information hiding techniques (steganography), potential perpetrators can quickly select, adapt and combine information hiding tools for their criminal activities.
Detecting this hidden information in...
10 January 2023 13h00-13h30
presented by the Members of ALICE, the Crypto group of the Mathematics department
In an increasingly digital world, cryptography is the only known solution to provide security in a cost-effective and scalable manner.
While mostly hidden to its users, cryptography p...
06 December 13h00-14h00
The past several years have presented numerous challenges for organizations of all types. The last year in particular emphasizes the importance of an organization’s capacity for change to drive performance and success in a volatile, uncertain, complex and ambiguous (VUCA)...
08 November 13h00-14h00
Le thème du webinar portera sur la recherche qui est actuellement menée sur les NEETs ( ‘not in employment, education or training’) par le Centre de recherche HIVA de la KU Leuven et la Chaire de Sociologie de l’ERM. Il s’agit donc des jeunes qui sont dans une situation fr...
04 October 13h00-14h00
Since the terrorist attacks in Zaventem and Maelbeek, TATP is probably the best known of all of the home-made explosives. It is no surprise that all aspects of this (and other) home-made explosives are investigated in the Laboratory for Energetic Materials and Blast Enginee...
06 September 13h00-14h00
Robotics has been changing our daily life since the 60s, starting with the development of industrial robots able to perform repetitive and painful tasks in a controlled environment. With the constant evolution of technology, such as the embedded computational power or the...
07 June 13h00-14h00
In view of the increase in illicit maritime activities like piracy, sea robbery, trafficking of narcotics, immigration and illegal fishing, an enhance of accuracy in surveillance is essential in order to ensure safer, cleaner and more secure maritime waterways. Recently, the f...
10 May 13h00-13h30
Na de capitulatie van Leopold III en zijn leger op 28 mei 1940, gebruikten de Franse, Britse en zelfs de Belgische regering deze daarna als zondebok. Dit besmeurde de reputatie van de hele Belgische krijgsmacht leidde tot de mythe dat het helemaal niet gevochten had, op enkele u...
20 Apr 13h00-14h00
Nuclear fusion on Earth would be the ideal solution for our future energy supply with almost unlimited ressources and excellent compatibility with the environment. The easiest fusion reaction on Earth is that between the hydrogen isotopes deuterium and tritium, and requires abou...
15 Mar 13h30-14h00
Cette seconde présentation portera sur l’interaction humain – systèmes autonomes, appliquée au domaine militaire. Les activités humaines sont aujourd’hui de plus en plus assistées par des systèmes dits (semi-)autonomes, et ce dans des domaines extrêmement variés (militaire, tran...
15 Mar 13h00-13h30
Ce séminaire visera dans un premier temps à fournir un aperçu des principales questions de recherche abordées en psychologie et en neurosciences appliquées au domaine militaire. Nous y aborderons notamment l’apport de la psychologie et des neurosciences cognitives dans l’optimi...
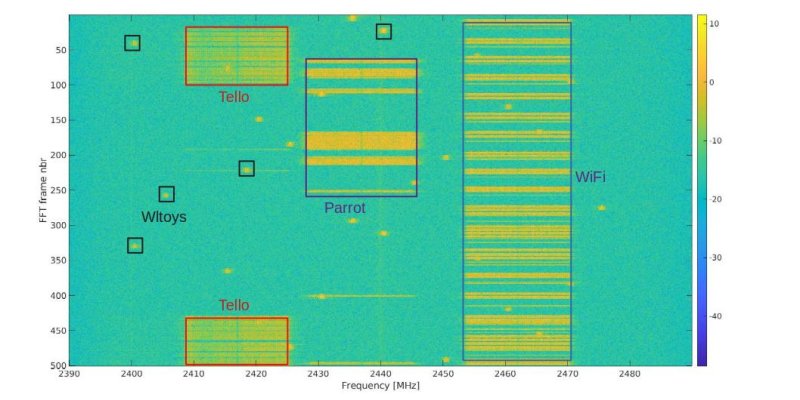
15 Feb 13h30-14h00
One of the most promising approaches to detect and classify UAVs is through sensing their RF communication with the ground control station. We will illustrate that, while the principle holds, the practical details can become extremely intricated owing to the complexity of the wa...
15 Feb 13h00-13h30
Counter-UAV technology, also known as counter-UAS, C-UAS, or counter-drone technology, refers to systems that are used to detect and/or neutralize unmanned aircraft. As concerns grow around the potential security threats, drones may create to both civilian and military interests...